 Silk Road 2.0 and 400 other sites believed to be selling illegal items including drugs and weapons have been shut down. The sites operated on the Tor network, which is a more secure software for Internet search – a system that also gives access to otherwise hard-to-reach parts of the net.
Silk Road 2.0 and 400 other sites believed to be selling illegal items including drugs and weapons have been shut down. The sites operated on the Tor network, which is a more secure software for Internet search – a system that also gives access to otherwise hard-to-reach parts of the net.
The joint operation between 16 European countries and the US saw 17 arrests, including Blake Benthall who is said to be behind Silk Road 2.0. Experts believe the shutdown represents a breakthrough for fighting cybercrime. Six Britons were also arrested, including a 20-year-old man from Liverpool, a 19-year-old man from New Waltham, a 30 year-old-man from Cleethorpes and a man and woman, both aged 58, from Aberdovey, Wales. All were interviewed and bailed according to the UK National Crime Agency.
As well as providing anonymous access to legitimate sites, Tor also lets people hide their visits to thousands of illegal marketplaces, trading in drugs, child abuse images as well as sites for extremist groups. It was the operation last year to take down the drugs marketplace Silk Road, which was the first major success in the battle against criminal use of the dark net.
Now this much bigger operation involving global cooperation amongst law enforcement agencies sees that battle taken to a new level, with Silk Road 2.0 amongst 400 sites closed. Still, the number of arrests may be telling – 400 sites closed, but just 17 arrests. That would suggest there is a lot of work still to be done. Silk Road 2.0 was resurrected after the original Silk Road site was shut down and its alleged owner arrested. The operation also saw the seizure of Bitcoins worth approximately $1m (£632,000).
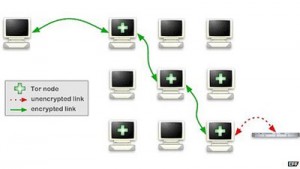 Tor is a special way to access the Internet that requires software, known as the Tor Browser bundle, to use it. The name is an acronym for The Onion Router – just as there are many layers to the vegetable, there are many layers of encryption on the network. It was originally designed by the US Naval Research Laboratory, and continues to receive funding from the US State Department.
Tor is a special way to access the Internet that requires software, known as the Tor Browser bundle, to use it. The name is an acronym for The Onion Router – just as there are many layers to the vegetable, there are many layers of encryption on the network. It was originally designed by the US Naval Research Laboratory, and continues to receive funding from the US State Department.
It attempts to hide a person’s location and identity by sending data across the Internet via a very circuitous route involving several “nodes” – which, in this context, means using volunteers’ PCs and computer servers as connection points. Encryption applied at each hop along this route makes it very hard to connect a person to any particular activity.
Tor hides a user’s identity by routing their traffic through a series of other computers. And Tor’s users include the military, law enforcement officers and journalists – who use it as a way of communicating with whistle-blowers – as well as members of the public who wish to keep their browser activity secret. But it has also been associated with illegal activity, allowing people to visit sites offering illegal drugs for sale and access to child abuse images, which do not show up in normal search engine results and would not be available to those who did not know where to look. bbc torproject
Many experts believe that this is an ongoing process and that Tor 3.0 which is now available will become more viable and sophisticated.
Source: Cyber Security Intelligence






















